Securely Connect Remote IoT P2P SSH Ubuntu: Your Ultimate Guide
Hey there, tech enthusiasts! If you're here, chances are you're looking to securely connect your remote IoT devices using P2P SSH on Ubuntu. Well, buckle up because we're diving deep into this topic. Whether you're a seasoned pro or just starting out, understanding how to set up a secure connection is crucial for protecting your IoT network. In this guide, we’ll break it down step by step so you can get it done right!
Imagine this: you’ve got a bunch of IoT devices scattered across different locations, and you need to manage them efficiently without compromising security. That’s where SSH comes in. It’s like having a secret tunnel that lets you access and control your devices remotely, all while keeping prying eyes at bay. But hey, there's more to it than just setting up SSH—especially when you're dealing with peer-to-peer (P2P) connections on Ubuntu.
Now, before we dive headfirst into the technicalities, let’s talk about why this matters. In today’s interconnected world, security is non-negotiable. Hackers are always on the prowl, looking for vulnerabilities to exploit. By securely connecting your remote IoT devices, you’re not just protecting your data—you’re also safeguarding your entire network. So, let’s get started, shall we?
Read also:Patricia Heaton Naked Unveiling The Truth Behind The Headlines
Understanding SSH: The Backbone of Secure Connections
SSH, or Secure Shell, is like the superhero of remote access protocols. It encrypts your data, ensuring that even if someone intercepts your communication, they won’t be able to make sense of it. For those of you who are new to this, SSH allows you to connect to a remote server or device securely, making it perfect for managing IoT devices.
Here’s why SSH is so awesome:
- It provides end-to-end encryption, keeping your data safe.
- It supports authentication methods like passwords and SSH keys, adding an extra layer of security.
- It’s widely supported across various platforms, including Ubuntu.
But wait, there’s more! SSH isn’t just about securing your connection—it also helps you automate tasks, transfer files, and even tunnel other protocols. Pretty cool, right?
Why Ubuntu is the Go-To Choice for SSH
Ubuntu is like the golden child of Linux distributions. It’s user-friendly, highly customizable, and comes with a ton of security features out of the box. When it comes to setting up SSH for IoT devices, Ubuntu is a no-brainer. Here’s why:
- It has excellent package management, making it easy to install and configure SSH.
- Its community is vast, meaning you’ll always find help if you run into issues.
- It’s lightweight, which is perfect for IoT devices with limited resources.
So, if you’re using Ubuntu as your base OS, you’re already on the right track. Now, let’s move on to the fun part: setting up P2P SSH connections.
Setting Up P2P SSH on Ubuntu: A Step-by-Step Guide
Alright, let’s get our hands dirty. Setting up a P2P SSH connection on Ubuntu might sound intimidating, but with the right steps, it’s a breeze. Here’s how you do it:
Read also:Vanessa Hudgens Leaks The Truth Behind The Headlines
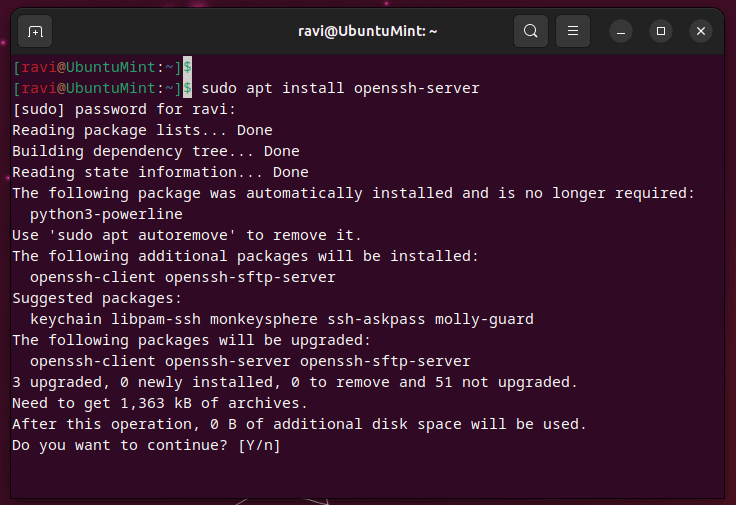
Step 1: Install SSH on Your Ubuntu System
First things first, you’ll need to make sure SSH is installed on your Ubuntu system. You can do this by running the following command in your terminal:
sudo apt update && sudo apt install openssh-server
This will install the OpenSSH server, which is what you’ll use to create your SSH connections.
Step 2: Configure SSH for Security
Now that SSH is installed, it’s time to tighten up your security settings. Here are a few things you should do:
- Change the default SSH port (usually 22) to something less obvious.
- Disable root login to prevent unauthorized access.
- Use SSH keys instead of passwords for authentication.
These steps might seem like overkill, but trust me, they’re worth it. Security is all about layers, and each of these adds an extra layer of protection.
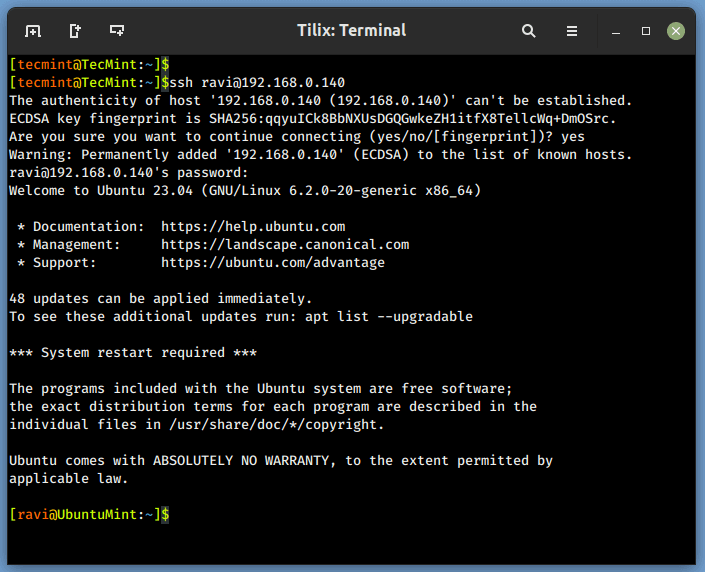
Step 3: Set Up Your IoT Devices
Next, you’ll need to configure your IoT devices to connect via SSH. This will vary depending on the devices you’re using, but generally, you’ll need to:
- Install an SSH client on your devices.
- Configure the devices to connect to your Ubuntu server.
- Test the connection to ensure everything is working as expected.
Once your devices are set up, you’ll be able to manage them remotely with ease.
Enhancing Security with SSH Keys
Using SSH keys instead of passwords is one of the best things you can do to enhance your security. Here’s how you set it up:
Generating SSH Keys
First, you’ll need to generate a pair of SSH keys. You can do this by running the following command:
ssh-keygen -t rsa -b 4096
This will create a public and private key pair. The public key will be shared with your devices, while the private key stays on your server.
Copying the Public Key
Once you’ve generated your keys, you’ll need to copy the public key to your IoT devices. You can do this using the following command:
ssh-copy-id user@device_ip
Replace user with your username and device_ip with the IP address of your device.
Troubleshooting Common SSH Issues
Even the best-laid plans can go awry, and SSH is no exception. Here are some common issues you might encounter and how to fix them:
Issue 1: Connection Timeout
If you’re getting a connection timeout error, it could be due to a firewall blocking your SSH port. Check your firewall settings and ensure that the port you’re using for SSH is open.
Issue 2: Permission Denied
This usually happens when your SSH keys aren’t set up correctly. Double-check that your public key is in the correct location on your device and that your private key is securely stored on your server.
Issue 3: Authentication Failed
If you’re getting an authentication failed error, it could be due to a mismatch between your public and private keys. Make sure you’re using the correct keys and that they haven’t been corrupted.
Best Practices for Secure IoT Connections
Now that you’ve got your SSH connection up and running, here are a few best practices to keep in mind:
- Regularly update your system and devices to patch any security vulnerabilities.
- Monitor your connections for any suspicious activity.
- Use strong, unique passwords for your devices.
By following these best practices, you’ll ensure that your IoT network remains secure and reliable.
Why Secure Connections Matter in IoT
In the world of IoT, security isn’t just a nice-to-have—it’s a necessity. With billions of devices connected to the internet, the potential for cyberattacks is enormous. By securing your connections, you’re not only protecting your data but also preventing your devices from being used in botnets or other malicious activities.
Think about it: if a hacker gains access to one of your IoT devices, they could potentially access your entire network. That’s why it’s crucial to take security seriously and implement measures like SSH to protect your devices.
Future Trends in IoT Security
As IoT continues to evolve, so too does the landscape of security. Here are a few trends to keep an eye on:
Trend 1: Blockchain for IoT Security
Blockchain technology is being explored as a way to enhance IoT security. By using blockchain, devices can securely share data without the need for a central authority.
Trend 2: AI-Driven Security Solutions
AI is being used to detect and respond to threats in real-time, making it an invaluable tool for securing IoT networks.
Trend 3: Zero-Trust Architecture
Zero-trust architecture assumes that no device or user can be trusted by default. This approach requires continuous verification, making it much harder for attackers to gain access.
Conclusion: Take Action Today
Alright, that’s a wrap! By now, you should have a solid understanding of how to securely connect your remote IoT devices using P2P SSH on Ubuntu. Remember, security is an ongoing process, so don’t be complacent. Stay informed, follow best practices, and always be on the lookout for new threats.
So, what are you waiting for? Go ahead and set up your SSH connections today. And don’t forget to leave a comment or share this article if you found it helpful. Until next time, stay secure and keep those IoT devices humming!
Table of Contents
- Securely Connect Remote IoT P2P SSH Ubuntu: Your Ultimate Guide
- Understanding SSH: The Backbone of Secure Connections
- Why Ubuntu is the Go-To Choice for SSH
- Setting Up P2P SSH on Ubuntu: A Step-by-Step Guide
- Enhancing Security with SSH Keys
- Troubleshooting Common SSH Issues
- Best Practices for Secure IoT Connections
- Why Secure Connections Matter in IoT
- Future Trends in IoT Security
- Conclusion: Take Action Today